Que sont les fuites WebRTC et comment les éviter ?

Avant de découvrir ce que sont les fuites WebRTC, nous devons savoir ce qu'est WebRTC. Alors, qu'est-ce que WebTRC ?
WebTRC est l'abréviation de Web Real Time Communication. Il s'agit d'un protocole Web open source désormais préinstallé dans de nombreux navigateurs Web et applications mobiles. Nous bTRC permet à ces navigateurs Web et applications mobiles de partager des informations entre eux en temps réel. Ces informations peuvent être des fichiers audio, vidéo ou même textuels.
WebRTC a été développé pour créer une méthode standardisée et efficace permettant la communication poste à poste en temps réel entre les navigateurs Web et certaines applications compatibles, sans nécessiter de plug-ins tiers ni d'installations complexes.
De nombreuses entreprises proposant aujourd'hui des services de visioconférence, d'appel vocal et de streaming en direct, telles que Google, Zoom, Facebook, Snap Inc. et UberConference, utilisent toutes le protocole WebRTC.
Comment fonctionne WebRTC ?
Maintenant que nous savons ce qu'est WebRTC, examinons rapidement son fonctionnement et mentionnons quelques applications concrètes.
WebRTC utilise un ensemble d'API JavaScript et de composants de navigateur intégrés pour fonctionner. Les principales API sont :
-
getUserMedia : utilisé pour accéder au microphone et à la caméra.
-
RTCPeerConnection : utilisé pour configurer les appels vidéo et audio.
-
RTCDataChannel : utilisé pour permettre le transfert de données peer-to-peer.
Avec ces API, voici une description rapide du fonctionnement de WebRTC :
1. Capture multimédia
La toute première étape du WebRTC est la capture des médias. Dans de nombreux cas, les médias sont les données qui doivent sp;être communiqué entre les navigateurs Web. Pour réaliser cela, lorsqu'une application WebRTC est lancée, l'API, getUserMedia demande l'accès à votre microphone et à votre caméra. Il apparaît généralement sous la forme d'un onglet contextuel sur votre navigateur avec le p;options « autoriser » et « bloquer ». Une fois autorisé, le média est capturé et prêt à être affiché ou transmis.
2. Signalisation
Bien que la signalisation ne soit pas particulièrement normalisée dans WebRTC, elle reste une étape cruciale de son fonctionnement. Avant d'établir la connexion, les navigateurs ou applications mobiles qui se connectent doivent échanger des informations qui sp;les aider à déterminer la meilleure façon d'établir une connexion. Ces informations peuvent être des messages de contrôle de session, des adresses réseau ou des données multimédias de session. La signalisation s'effectue généralement via WebSocket, HTTP ou d'autres protocoles similaires.
3. Créer une connexion
La prochaine API utilisée par WebRTC estRTCPeerConnection. Avec cette API, les paramètres de connexion, tels que le codec et d'autres paramètres multimédias, sont négociés et convenus. Après cela, WebRT C utilise le cadre ICE (Interactive Connectivity Establishment) pour déterminer le meilleur chemin pour se connecter à ses homologues, et une connexion directe d'égal à égal est établie.
4. Transfert de données
Une fois la connexion établie, les données multimédias, qui peuvent être des fichiers audio, vidéo ou même texte, peuvent désormais être transmises entre homologues en temps réel. Les données sont également chiffrées. Protocole SRTP (Secure Real-time Transport Protocol) pour les données multimédias et DTLS (Datagram Transport Layer Security) pour les données non multimédias. Cela garantit que les données sont protégées et sécurisées pendant le transfert. />
5. Communication médiatique
Pendant le transfert des données multimédias, les composants WebRTC gèrent les bandes passantes, l'encodage et le décodage des médias, les réductions de bruit, les annulations d'écho et les fluctuations du réseau.
6. Communication du canal de données
La dernière API WebRTC,RTCDataChannel, est ce qui gère cette partie. Cette partie couvre le transfert d'autres formes de données en dehors des médias. Ces données peuvent être des conversations textuelles, des données de jeu ou des transferts de fichiers.
7. Fin de session
Une fois la communication terminée, la session est terminée à l'aide du même processus de signalisation que celui utilisé pour l'établir.
Maintenant que nous savons comment fonctionne WebRTC, listons quelques-unes de ses applications réelles :
-
La plateforme de jeu de Google, Stadia.
-
Internet des objets.
-
Transfert de fichiers dans Torrents.
-
Applications financières et plateformes de trading.
-
Réalité augmentée et virtuelle.
-
Appels vocaux et vidéo.
-
Support client et chats en direct.
-
Éducation en ligne et e-learning.
Que sont les fuites WebRTC ?

Sachant que les connexions WebRTC nécessitent l'échange et le transfert d'informations confidentielles pendant la phase de signalisation et de création de connexion, nous pouvons déduire ce qui se passe lors d'une fuite WebRTC.
Alors, que sont les fuites WebRTC ? Les fuites WebRTC sont des failles de sécurité qui se produisent lors d'un transfert WebRTC et qui peuvent entraîner l'exposition de votre adresse IP.
Votre adresse IP est un élément essentiel de votre anonymat en ligne et, si elle est compromise, elle pourrait exposer votre localisation et vos FAI (fournisseur d'accès à Internet). Ces informations, entre les mains de pirates malveillants pourraient vous causer de nombreux problèmes.
Les fuites WebRTC sont certainement dangereuses lorsqu'elles se produisent et si vous utilisez des navigateurs tels que Firefox, Opera, Chrome, Microsoft Edge et Opera, vous courez un risque plus élevé d'être victime de ces fuites. Principalement parce que ces navigateurs Web sont livrés avec WebRTC activé par défaut.
Comment vérifier les fuites WebRTC
Voici quelques méthodes pour détecter les fuites WebRTC :
1. Tests de fuites WebRTC en ligne
À l'heure actuelle, il existe plusieurs tests de fuites WebRTC en ligne que vous pouvez utiliser pour vérifier si vous avez des fuites sur votre navigateur. Parmi les plus populaires, on trouve :
2. Tests de fuite WebRTC manuels
Si vous ne faites pas entièrement confiance aux tests de fuite WebRTC en ligne, vous pouvez effectuer une vérification manuelle. Le processus est assez fastidieux, mais voici une explication rapide de la procédure à suivre pour effectuer un test de fuite WebRTC manuel sur Chrome.
-
Ouvrir une nouvelle fenêtre Chrome en mode navigation privée

-
Faites un clic droit sur la fenêtre et sélectionnez « inspecter la page ». Cela devrait ouvrir les outils de développement.

-
Lorsque cela s'affiche, accédez à l'onglet « Console ».

-
Copiez et collez ce code :
var rtc = window.RTCPeerConnection || window.mozRTCPeerConnection || window.webkitRTCPeerConnection; var pc = new rtc({ iceServers: [] }); pc.createDataChannel(""); pc.createOffer(pc.setLocalDescription.bind(pc), function() {}); pc.onicecandidate = function(ice) { console.log("Adresse IP : " + ice.candidate.candidate.split(" ")[4]); };
-
Tapez « autoriser le collage » et exécutez le code.

Après avoir exécuté le code, si l'adresse IP qui s'affiche est votre adresse IP réelle, vous risquez de subir une fuite WebRTC. (Vous pouvez vérifier votre adresse IP)ici.)
Ce processus est uniquement destiné à Google Chrome sur Windows et Mac. Les autres navigateurs sont beaucoup plus difficiles à vérifier, mais nous aborderons la manière d'empêcher les fuites WebRTC sur ces autres navigateurs dans le “ Comment bloquer les fuites WebRTC ” section de cet article.
3. Utilisez les extensions de navigateur de test de fuites WebRTC
La dernière méthode pour vérifier les fuites WebRTC consiste simplement à ajouter des extensions de navigateur à votre navigateur et à les exécuter. Parmi les plus réputées, on trouve WebRTC Control (Chrome, Firefox) etuBlock Origin.
Comment prévenir les fuites WebRTC
Voyons comment prévenir les fuites WebRTC :
1. Désactivez WebRTC sur votre navigateur
Voyons comment désactiver WebRTC sur les versions de bureau de ces navigateurs.
Comment désactiver WebRTC sur le navigateur Firefox
-
Saisissez about:config dans la barre d'adresse
-
Cliquez sur le bouton « J'accepte les risques ! » ” bouton
-
Tapez media.peerconnection.enabled dans la barre de recherche
-
Double-cliquez pour modifier la valeur en « false »
Comment désactiver WebRTC sur le navigateur Opera
-
Accédez aux paramètres de votre navigateur Opera
-
Développez la section Avancé sur le côté gauche et cliquez sur Confidentialité et sécurité
-
Faites défiler vers le bas jusqu'à WebRTC et sélectionnez le bouton radio Désactiver UDP non proxy
-
Fermez l'onglet et les paramètres devraient être enregistrés automatiquement.
Comment désactiver WebRTC sur le navigateur Microsoft Edge
Il n'existe aucun moyen de désactiver à 100 % WebRTC sur votre navigateur Edge, mais vous pouvez masquer votre adresse IP lors des connexions WebRTC comme ceci :
-
Tapez about:flags dans la barre d'adresse
-
Cochez l'option « Masquer mon adresse IP locale sur les connexions WebRTC »
2. Utiliser les extensions de navigateur
La méthode des extensions de navigateur pour empêcher les fuites WebRTC fonctionne pour les navigateurs Chrome et Firefox. Et tout comme pour les tests de fuites WebRTC, les extensions les plus réputées pour empêcher les fuites WebRTC sont WebRTC Control (Chrome, Firefox) etuBlock Origin. Il y a aussi Limiteur de réseau WebRTC pour Chrome.
3. Utilisez un proxy ou VPN
Un excellent VPN pourrait très bien masquer votre adresse IP. Ainsi, même en cas de fuite WebRTC, l'adresse IP divulguée devient ;s'avère être un faux. Certains excellents VPN, comme ExpressVPN, vous permettent également de désactiver de force WebRTC dans vos navigateurs à l'aide de leurs extensions pour Chrome, Firefox, etEdge. Les autres VPN que vous pouvez essayer incluent SurfShark VPN, et NordVPN.
4. Utilisez un navigateur anti-détection
Le dernier et peut-être le meilleur moyen de vous protéger des fuites WebRTC est d'utiliser un très bon navigateur anti-détection. Un bon Le navigateur antidetect fait bien plus que masquer votre adresse IP ; il usurpe également vos empreintes digitales numériques. Vous rendant ainsi 100 % anonyme pendant votre navigation.
Options de prévention des fuites WebRTC dans AdsPower
Ouvrez lel'application AdsPower et accédez à la page des paramètres du profil du navigateur. Vous y trouverez WebRTC dans le Section Avancé. Nous vous guiderons à travers les quatre méthodes permettant d'éviter les fuites WebRTC dans AdsPower :
-
Transférer : Transférer via Google pour masquer l'adresse IP réelle. Utilisé pour les sites Web hautement sécurisés (Ebay et Discord).

-
Remplacer : WebRTC activé. L'adresse IP publique sera remplacée par l'adresse IP proxy et l'adresse IP locale sera masquée.

-
Réel : WebRTC activé. Votre adresse IP réelle sera utilisée.

-
Désactiver : WebRTC fermé. Le site Web détectera que vous fermez WebRTC.
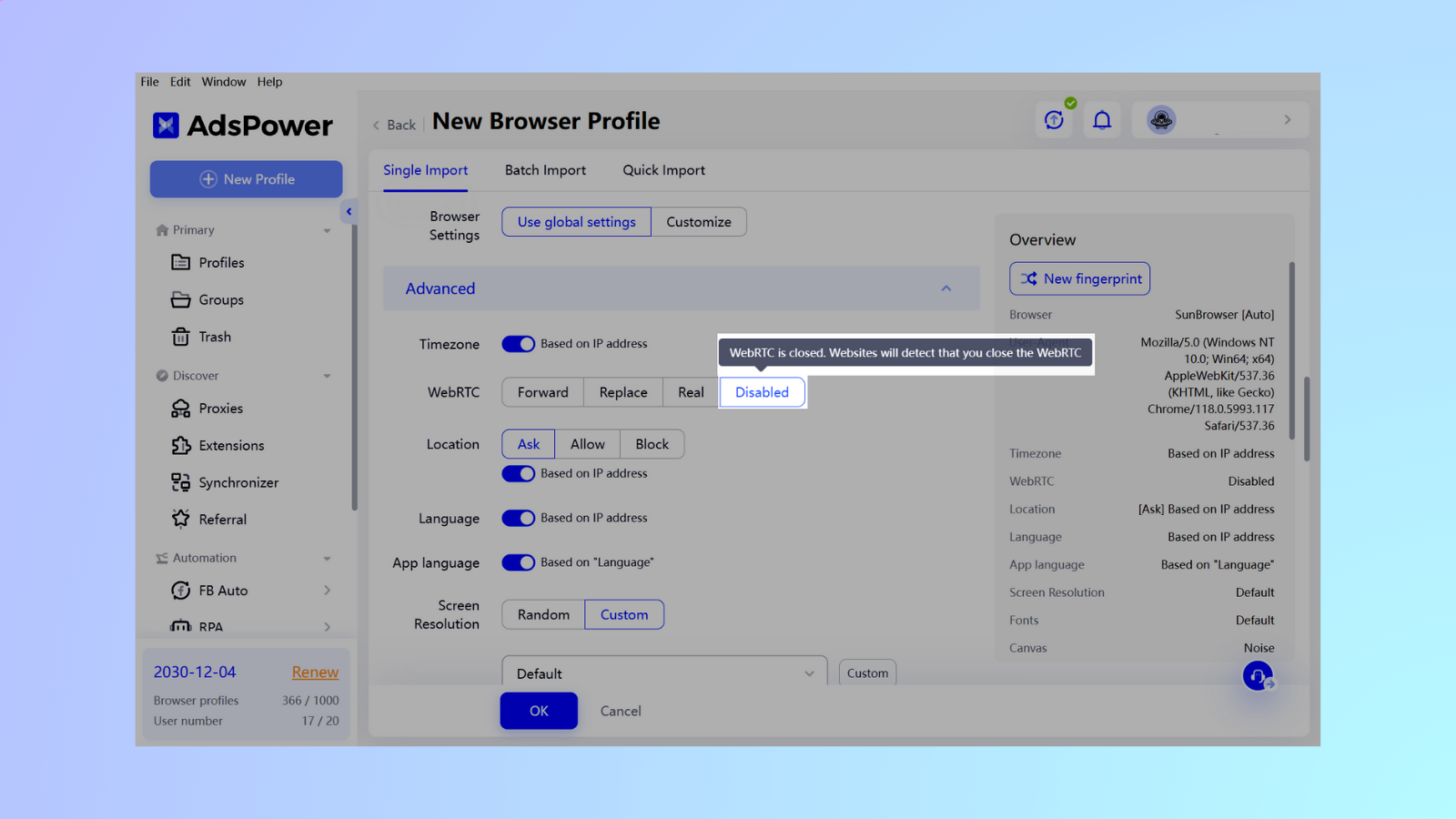
Le masquage WebRTC peut offrir des exigences de confidentialité plus strictes dans certains cas en contournant les serveurs proxy pour certaines données, comme les médias. Cependant, ce mode de transfert nécessite une tran transmission de données via un serveur de transit, ce qui peut potentiellement ralentir la communication. L'impact sur la vitesse augmente avec un masquage plus strict : Désactiver > Transférer > Remplacer > Réel.
Trouver l'équilibre : le niveau de masquage que vous choisissez dépend de vos priorités. Si l'anonymat est primordial, des mesures plus strictes Les paramètres peuvent valoir la peine de subir quelques désagréments occasionnels. Mais si un accès transparent au site web est crucial, une approche plus légère pourrait être préférable.
Conclusion
Vous devriez désormais savoir à quel point WebRTC est utile et comment les fuites WebRTC pourraient finir par exposer votre adresse IP aux mauvaises personnes. Vous Vous devez également savoir comment effectuer des tests de fuite WebRTC pour savoir si vous êtes exposé à un risque de fuite WebRTC et comment les prévenir.
Tout cela étant dit, bien qu'il existe de nombreuses méthodes individuelles sur cette liste pour prévenir les fuites WebRTC, il serait préférable d'opter pour une combinaison de deux ou bsp;plus de méthodes de prévention juste pour être plus certain. Et si cela semble un compliqué, il d'utiliser un navigateur antidétection, en particulier AdsPower, et vous pouvez être assuré que votre anonymat en ligne restera intact.

Les gens lisent aussi
- Comment le Fingerprinting Bloque vos Comptes (et comment AdsPower l'évite)

Comment le Fingerprinting Bloque vos Comptes (et comment AdsPower l'évite)
Pourquoi les incohérences d'empreinte causent des bannissements et comment l'architecture double moteur d'AdsPower avec cœurs natifs protège vos sessions.
- Les 8 meilleures alternatives à Whoer en 2025 (outils de vérification d'adresse IP précis et confidentiels)
Les 8 meilleures alternatives à Whoer en 2025 (outils de vérification d'adresse IP précis et confidentiels)
Vous cherchez une alternative à Whoer.net ? Découvrez notre liste 2025 des 8 meilleurs outils de vérification d’adresse IP pour une analyse d’empreinte numérique précise et privée et une navigation en ligne améliorée.
- RDP vs Antidetect Browser : quelle est la différence et lequel est le plus sécurisé ?
RDP vs Antidetect Browser : quelle est la différence et lequel est le plus sécurisé ?
Utilisez-vous le protocole RDP ou un navigateur antidétection pour gérer vos comptes ? Découvrez les différences entre RDP et un navigateur antidétection et apprenez à choisir la solution la plus adaptée à vos besoins.
- Décryptage de ce qu'est un agent utilisateur : composants UA et comment les rechercher

Décryptage de ce qu'est un agent utilisateur : composants UA et comment les rechercher
Découvrez ce qu'est un agent utilisateur, ses composants et comment trouver la chaîne UA de votre navigateur dans ce blog.
- Comment éviter les empreintes digitales du navigateur : un guide complet

Comment éviter les empreintes digitales du navigateur : un guide complet
Vous vous inquiétez de l'empreinte digitale de votre navigateur ? Notre guide vous aide à l'éviter tout en révélant un minimum d'informations personnelles.